Module 1 Task 4
Section Overview:
You can find more information about NSX-T capabilities in VMware’s website under VMware NSX-T Data Center Documentation.
In this Section, you will learn just a few additional NSX-T Advanced Features. You will learn how to:
Create NSX-T tags for VMs
Create NSX-T groups based on tags
Create Distributed Firewall Rules in NSX-T
NSX-T Tags
NSX-T Tags help you label NSX-T Data Center objects so that you can quickly search or filter objects, troubleshoot and trace, and do other related tasks.
You can create tags using both the NSX-T UI available within AVS and APIs.
More information on NSX-T Tags can be found here: VMware NSX-T Data Center Documentation.
Exercise 1: Assign NSX-T Tags to VMs
Two Test VMs required
Please make sure that you have created 2 Test VMs as explained in the previous Task before you proceed in this exercise.Step 1: Assign Tags to your VMs
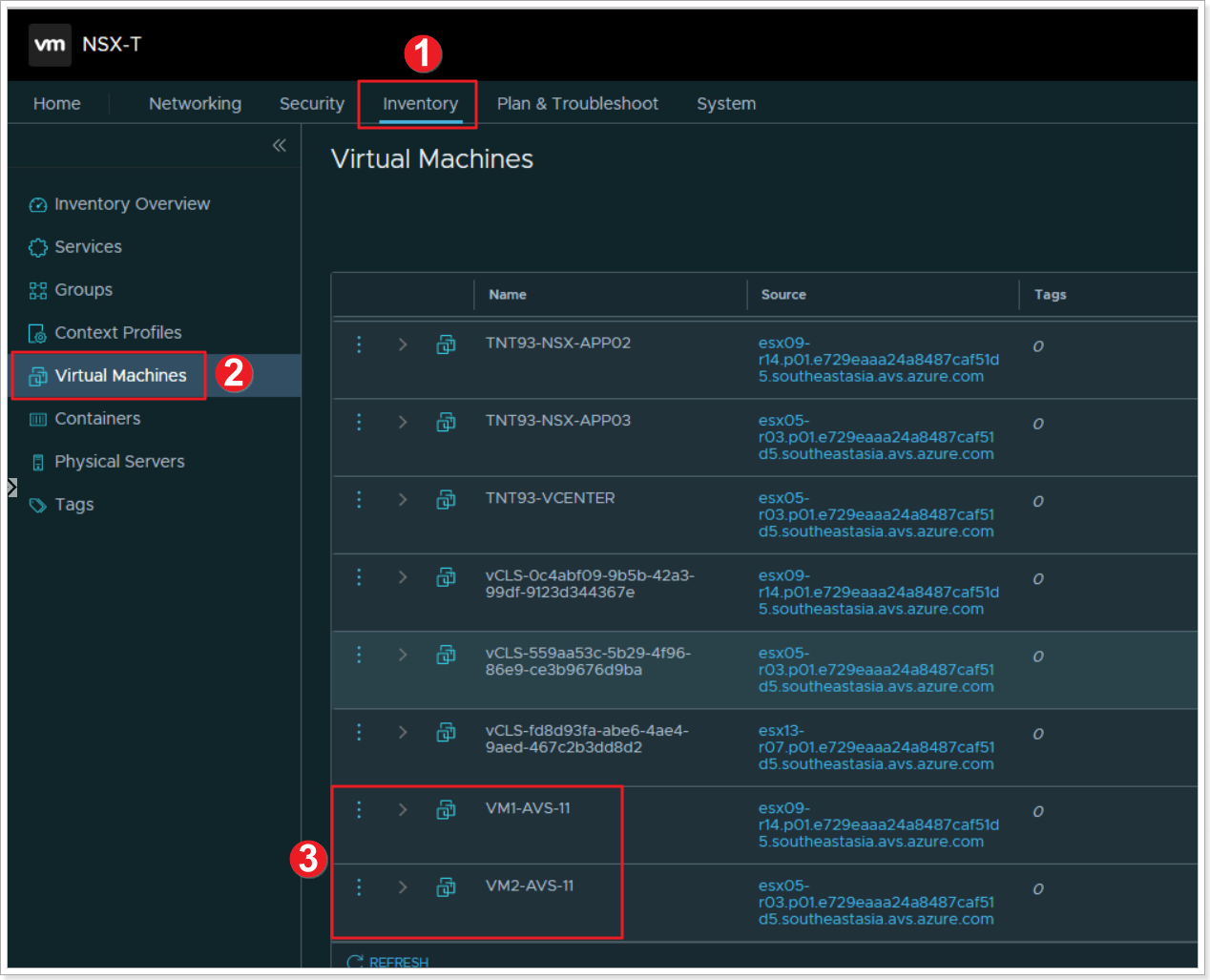
- From the NSX-T UI, click Inventory.
- Click Virtual Machines.
- Locate your 2 Virtual Machines you created in the previous task, notice they have no tags.
Click the elipsis next to the first VM and click Edit.
Step 2: Name your VM’s tag
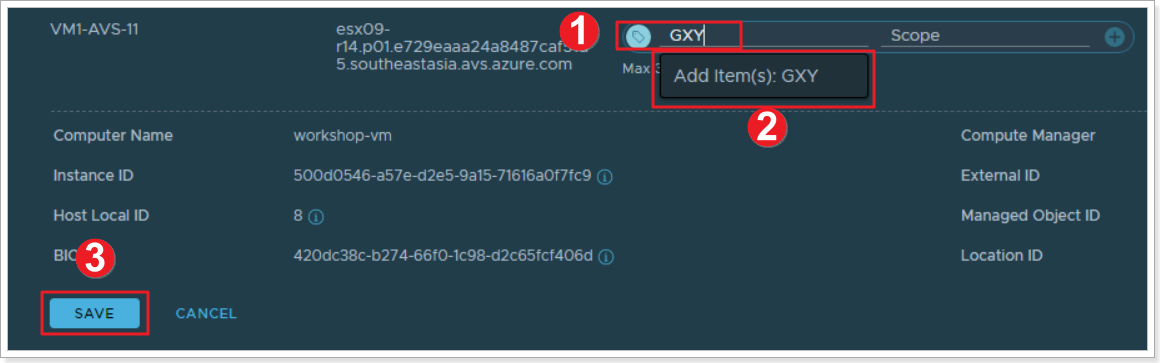
- Type “GXY”, where X is your group number and Y is your participant number.
- Click to add GXY as a tag to this VM.
- Click SAVE.
REPEAT THE ABOVE STEPS FOR VM2 USING THE SAME TAG.
NSX-T Groups
Groups include different objects that are added both statically and dynamically, and can be used as the source and destination of a firewall rule.
Groups can be configured to contain a combination of Virtual Machines, IP sets, MAC sets, segment ports, segments, AD user groups, and other groups. Dynamic including of groups can be based on a tag, machine name, OS name, or computer name.
You can find more information on NSX-T Groups on VMware’s NSX-T Data Center docs.
Exercise 2: Create NSX-T Groups
Step 1: Create an NSX-T Group
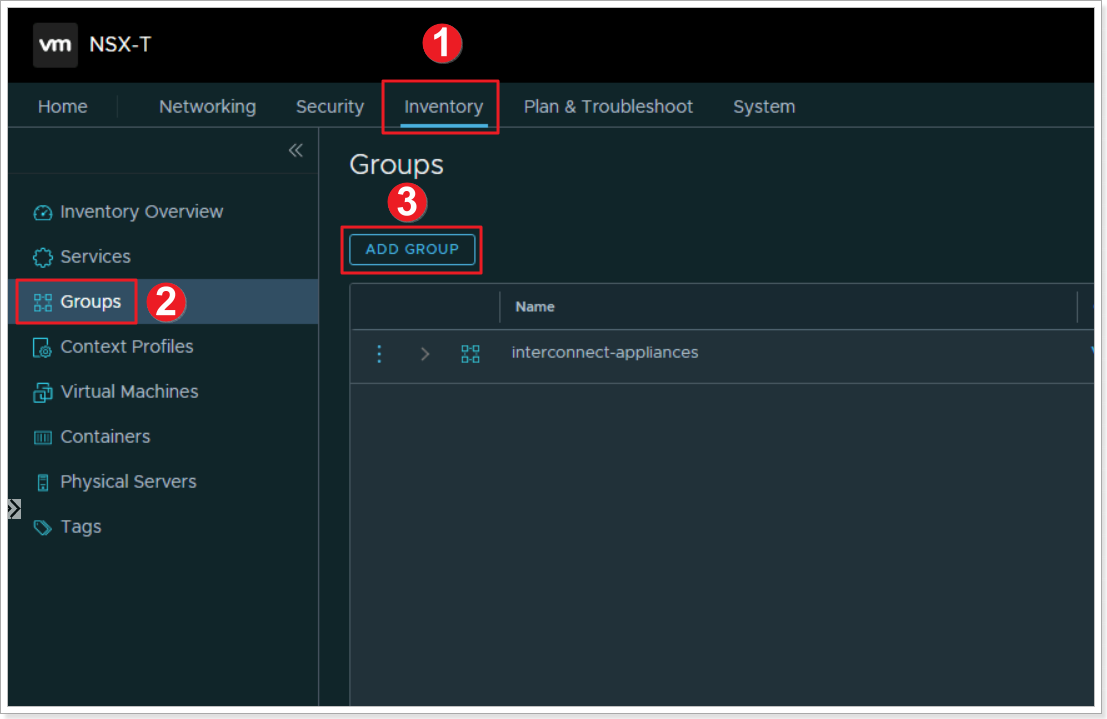
Now that we’ve assigned tags to the VMs, we’ll create a group based of those tags.
- Click Inventory
- Click Groups
- Click ADD GROUP
Step 2: Name your NSX-T Group and Assign Members
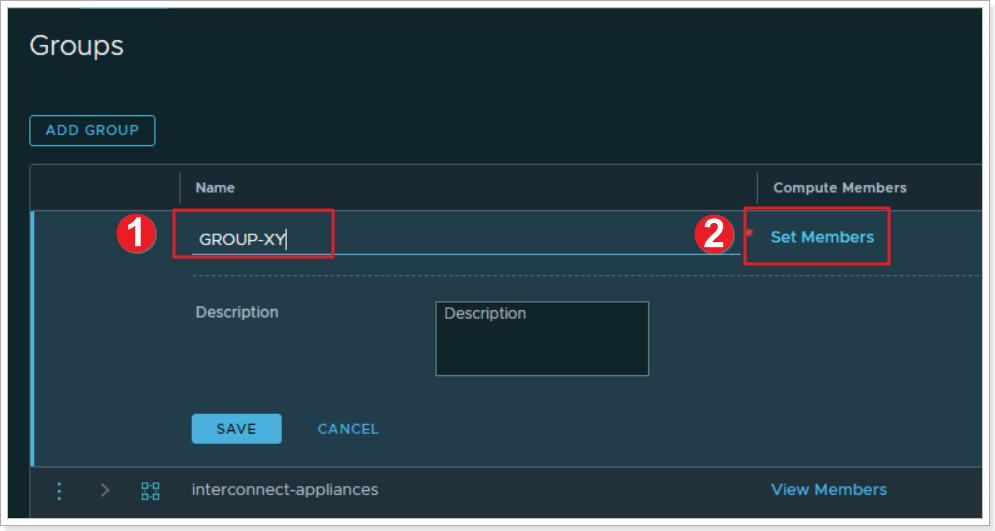
- Name your group GROUP-XY where X is your group number and Y is your participant number
- Click on *Set Members
Step 3: Set the Membership Criteria for your Group
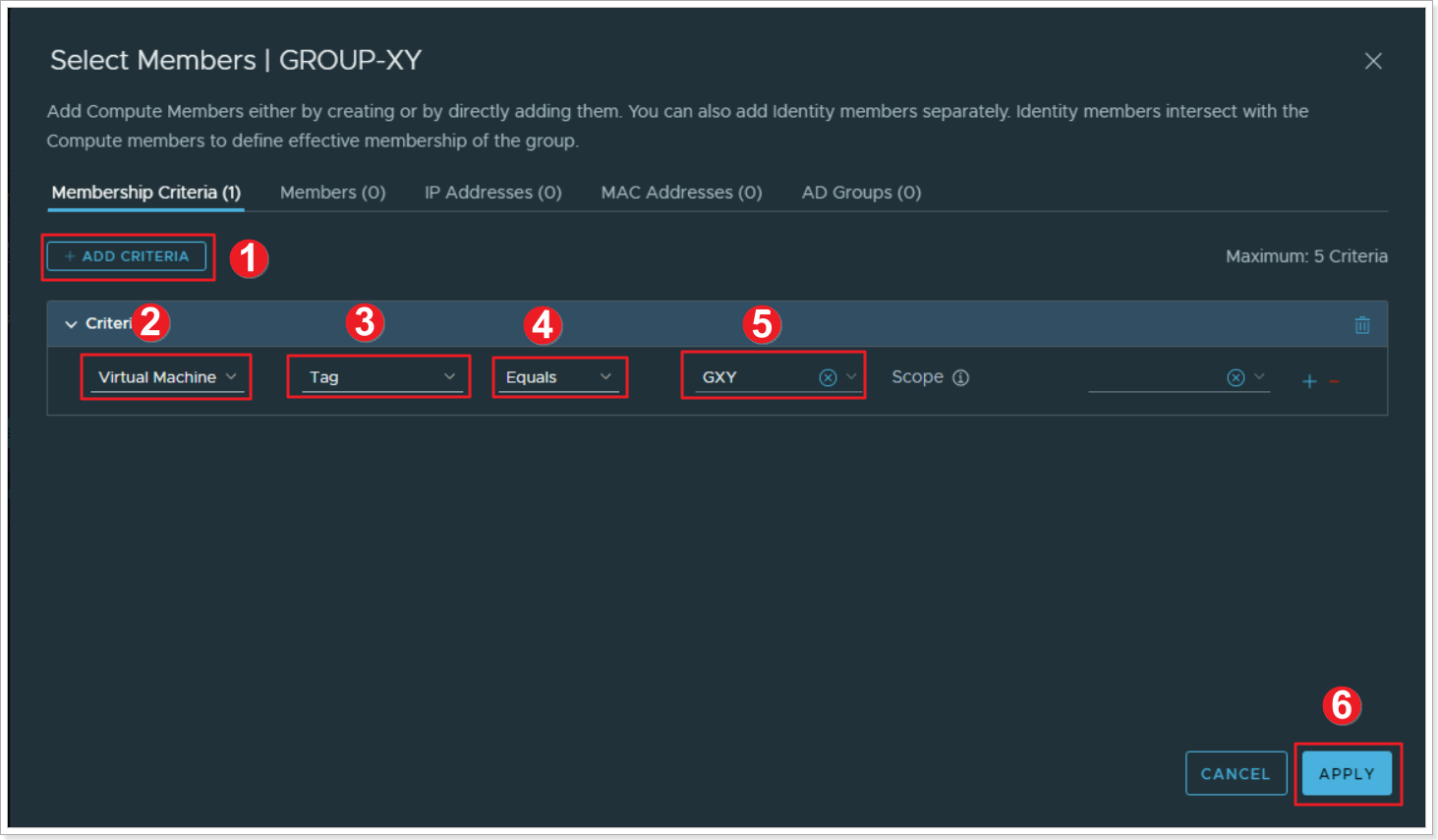
- Click ADD CRITERIA
- Select Virtual Machine
- Select Tag
- Select Equals
- Select your previously created group GXY
- Click APPLY. Then click SAVE
NSX-T Distributed Firewall
NSX-T Distributed Firewall monitors all East-West traffic on your AVS Virtual Machines and allows you to either deny or allow traffic between these VMs even if the exist on the same NSX-T Network Segment. This is the example of your 2 VMs and we will assume they’re 2 web servers that should never have to talk to each other. More information can be found here: Distributed Firewall.
Exercise 3: Create an NSX-T Distributed Firewall Policy
Step 1: Add a Policy
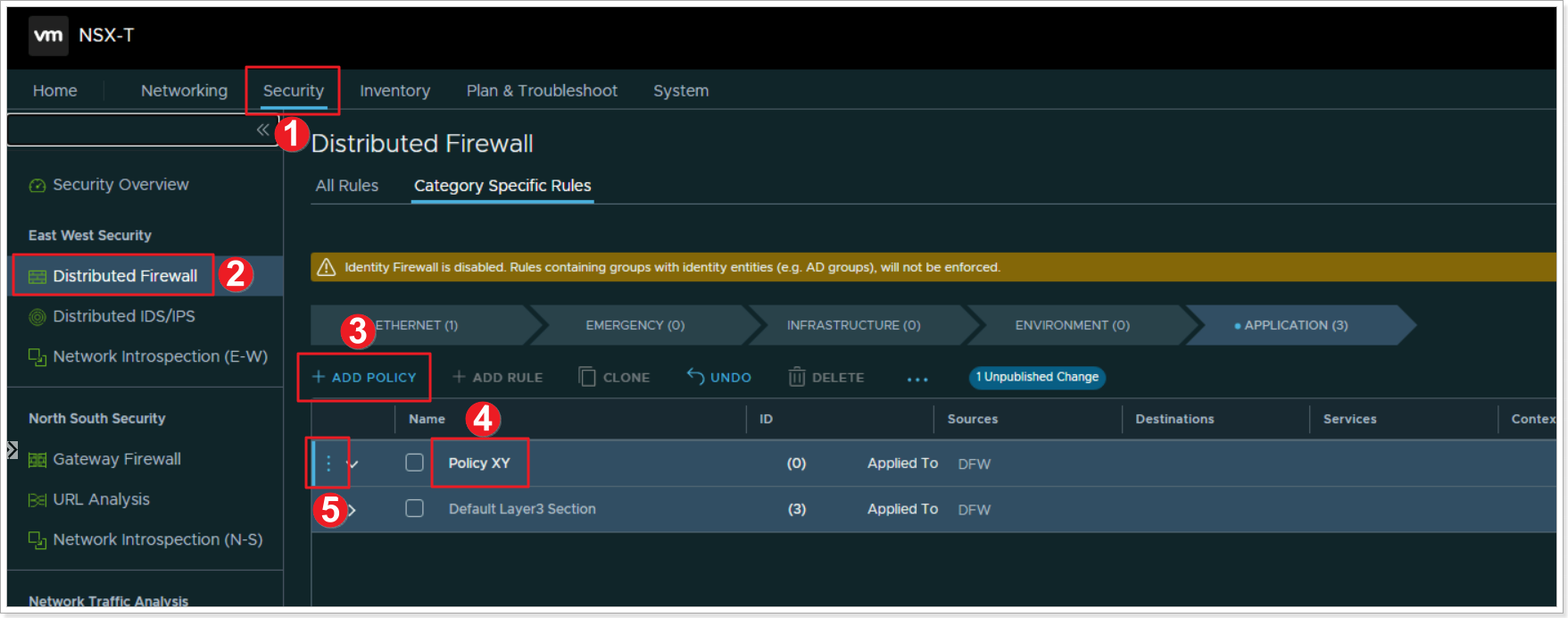
- Click Security
- Click Distributed Firewall
- Click + ADD POLICY
- Give your policy a name “Policy XY” where X is your group number and Y is your participant number
- Click the elipsis and select Add Rule
Step 2: Add a Rule
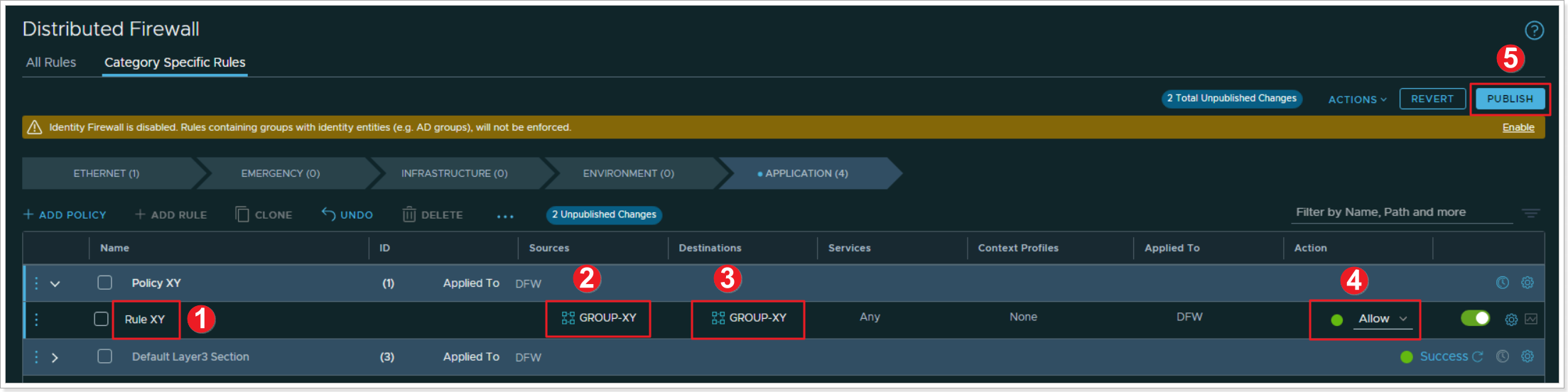
- Name your rule “Rule XY”
- Click under Sources column and select your newly created “GROUP-XY”
- Click under Destinations and also select “GROUP-XY”
- Leave all other defaults, and for now, leave the Action set to Allow. We will change this later to understand the behavior
- Click PUBLISH to publish the newly created Distributed Firewall Rule
Step 3: Reject communication in your Distributed Firewall Rule
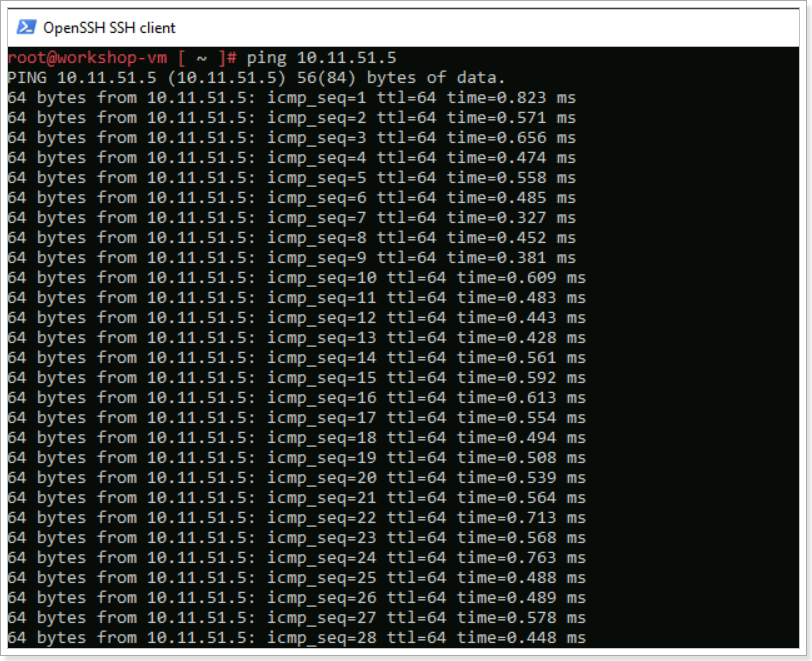
Hopefully you still have the SSH sessions open to your 2 VMs you created earlier. If not, just SSH again. From one of the VMs, run a continuous ping to the other VM’s IP address like the example below.
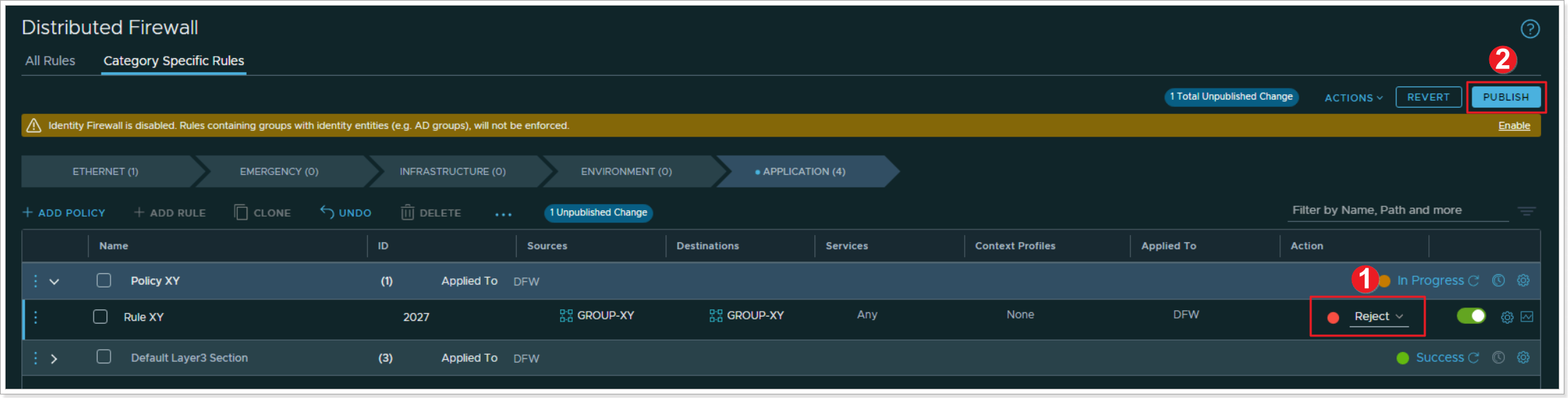
- Change the Action in your Rule to Reject
- Click PUBLISH
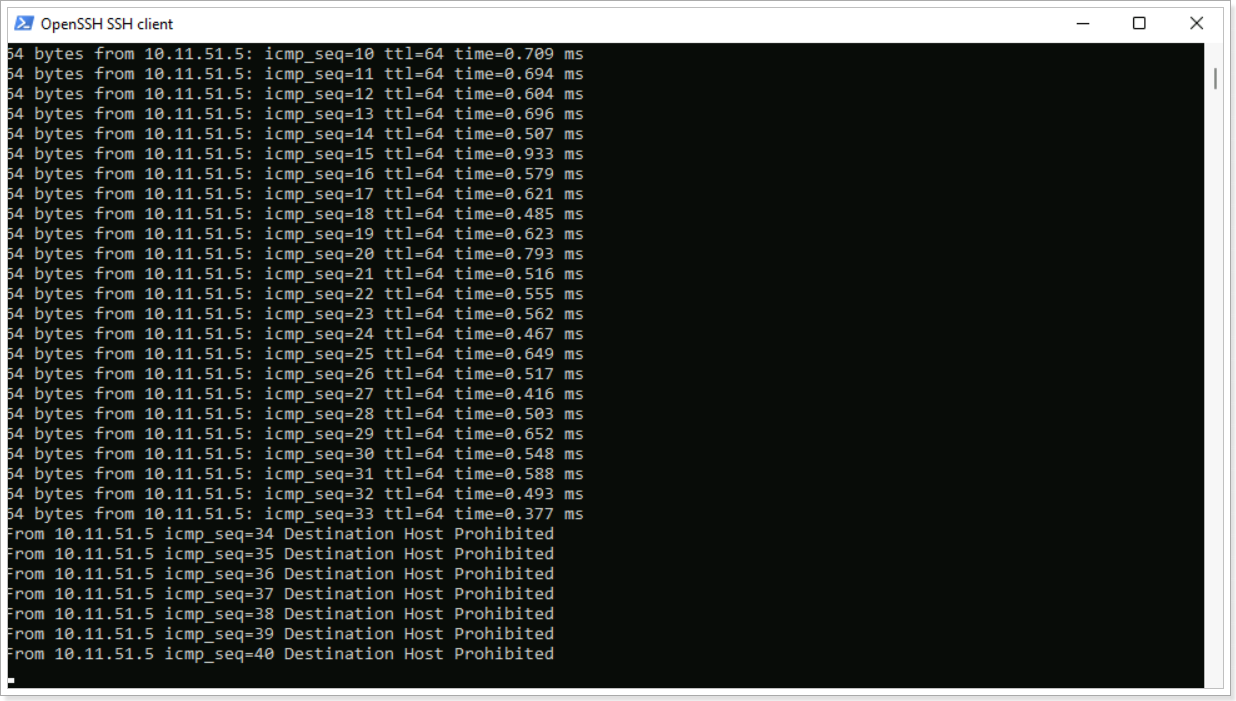
You can notice that after publishing the change to Reject on your rule, the ping now displays “Destination Host Prohibited”. NSX-T DFW feature is allowing the packet to get from one VM to another but it rejects it once the second VM receives the packet. You can also change this option to Drop where the packet is completely dropped by the second VM.
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.